Threat Protection: Proactively detect and eliminate vulnerabilities
Systematically implement cyber security and proactively prevent or mitigate damage
Through proactive vulnerability, change and risk detection, octoplant, as part of the complete security architecture, protects production processes from attacks and prevents damage and production downtime. With the help of octoplant, damage can be prevented, or the impact reduced.
Today, no company can rule out the possibility of being targeted by cyber attacks, which increasingly affect operational technology (OT) in industrial plants. Proactive protection measures are essential to reduce downtime, errors, and safety hazards. As part of risk analyses of the entire plant, weak points can be identified and eliminated based on the device inventory.

Besides all the benefits of connected machines and industrial plants, it also bears a considerable risk. If manufacturers don't monitor their industrial automation assets with all their details, they lack any basis for recognizing vulnerabilities.
Features of octoplant Threat Protection

Create vulnerability report
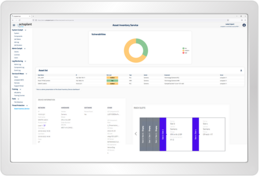
Receive a complete vulnerability exposure overview of your assets, incl. mitigation recommendation.

Identify and proactively close security gaps and risks
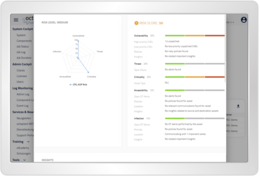
With octoplant's threat protection features, you can get an overview of vulnerabilities in the entire plant as well as individual devices. See which devices are considered risky and reduce risks and hidden vulnerabilities.
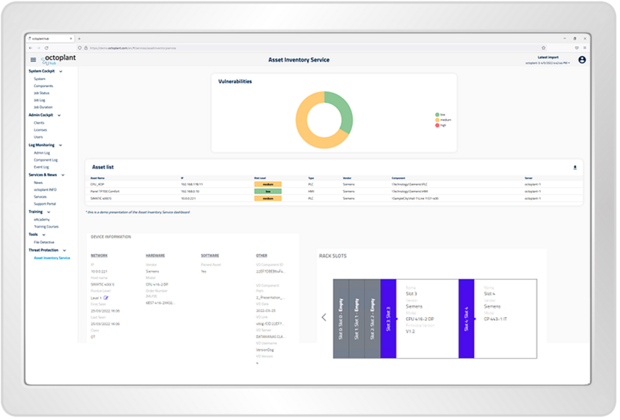
The devices connected in octoplant are automatically updated and added to the asset list with all existing information. This makes it easy to eliminate gaps in your disaster recovery strategy. Metadata from octoplant, such as the component path or the latest version, is also stored to facilitate asset mapping.
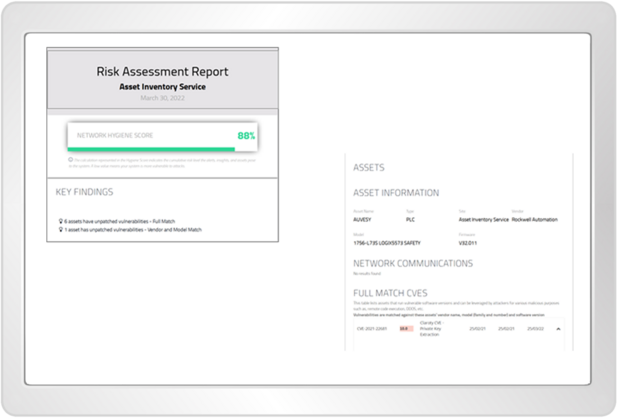
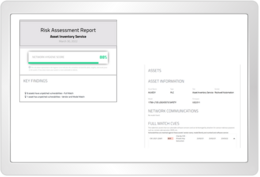
Get a detailed risk assessment report for your assets. This includes manufacturer, model number, firmware and the latest CVE data (CVE = Common Vulnerabilities and Exposures).
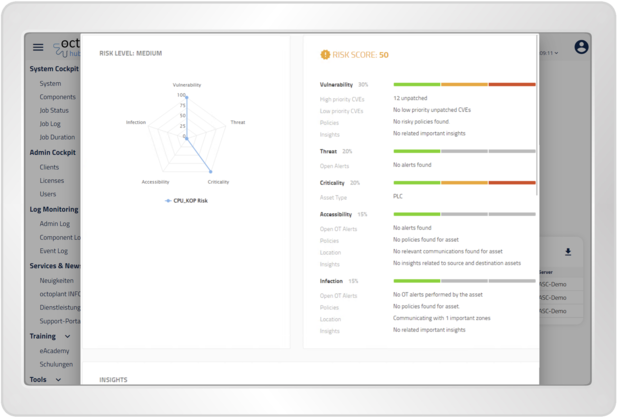
octoplant provides a detailed asset risk assessment with automatic mapping and continuous updating for each asset in the inventory. The details of each asset are compared against the latest Common Vulnerabilities and Exposures (CVE) data and an extensive library of insecure protocols, misconfigurations and other vulnerabilities.
Frequently asked questions
- hardware
- firmware
- model
- rack slot
- IP
- manufacturer
- and more
More information about the CVSS score can be found under the following public link: